Cyber espionage programs produced by Israeli Espionage Companies have been deciphered in many countries, including the USA. Governments or intelligence services that buy Pegasus from NSO and Predator from Cytrox can access the phones of anyone they want. Through these programs, conversations and correspondence on the phones are tracked, and instant access to photos and locations can be provided.
Many independent journalists and dissidents have filed lawsuits in the USA and Europe on this issue, and the news on this issue has occupied the agenda in the past months.
The last example of these events emerged with the Egyptian Dissident and Former Presidential Candidate Ayman Nur.
Ayman Nur also made statements to the Arabi21 news platform regarding the Espionage incident, which was uncovered and examined in detail by Toronto-based Citizen Lab.
You can read the detailed report made by Citizen Lab by clicking the link https://citizenlab.ca/2021/12/pegasus-vs-predator-dissidents-doubly-infected-iphone-reveals-cytrox-mercenary-spyware/. The report explains in detail how Android and Apple systems were infiltrated, which computer codes were used, and briefly states the following:
Two Egyptians—exiled politician Ayman Nour and the host of a popular news program (who wishes to remain anonymous)—were hacked with Predator spyware, built and sold by the previously little-known mercenary spyware developer Cytrox.
The phone of Ayman Nour was simultaneously infected with both Cytrox’s Predator and NSO Group’s Pegasus spyware, operated by two different government clients.
Both targets were hacked with Predator in June 2021, and the spyware was able to infect the then-latest version (14.6) of Apple’s iOS operating system using single-click links sent via WhatsApp.
We obtained samples of Predator’s “loader,” the first phase of the spyware, and analyzed their functionality. We found that Predator persists after reboot using the iOS automations feature.
We conducted Internet scanning for Predator spyware servers and found likely Predator customers in Armenia, Egypt, Greece, Indonesia, Madagascar, Oman, Saudi Arabia, and Serbia.
Cytrox was reported to be part of Intellexa, the so-called “Star Alliance of spyware,” which was formed to compete with NSO Group, and which describes itself as “EU-based and regulated, with six sites and R&D labs throughout Europe.”
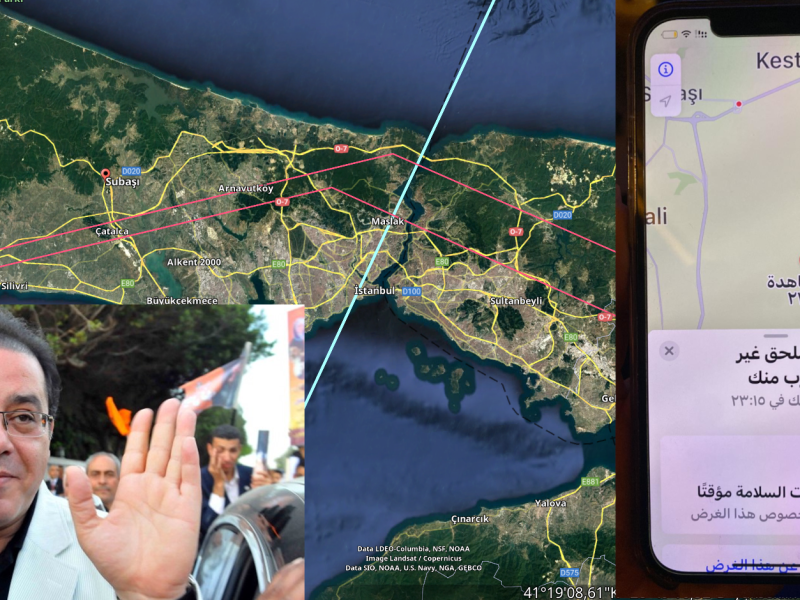
You can reach Ayman Nur’s interview by clicking on the link https://arabi21.com/story/1405942/. The Egyptian Dissident has also released many phone screen prints of its monitoring. One of these phone printouts is about being watched in the Kestanelik, Subaşı region of Istanbul. This shows that Dissidents, Independent Journalists and Politicians can be monitored via phones no matter what country they are in.